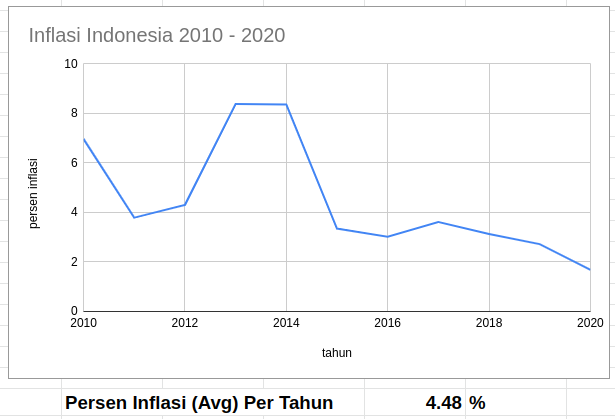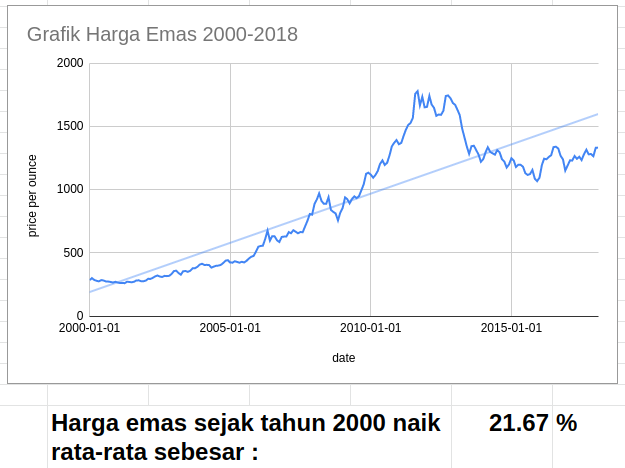
Insiden hacking PDNS yang baru terjadi ini bukan suatu yang mengejutkan bagi mereka yang paham tentang kondisi cybersecurity di Indonesia. Misalnya, laporan “Hi-Tech Crime Trends Report 2023/2024” menyatakan bahwa Indonesia adalah juara / paling banyak mengalami insiden Ransomware di ASEAN. Sangat disayangkan, tapi itulah faktanya.
Di sisi lain, Indonesia menyimpan segudang talent / bakat luar biasa di bidang Cybersecurity ini. Sudah banyak yang muncul, ataupun memilih tidak muncul. Selalu ada harapan bahwa Indonesia bisa.
CYBERSECURITY
Topik ini terkesan sangat rumit dan sulit. Dan berbagai tokoh yang muncul juga tidak membantu, banyak yang malah memilih menebar jargon dan istilah-istilah yang memusingkan, sehingga terkesan cerdas – namun, tidak bermanfaat bagi masyarakat. Padahal cybersecurity itu seharusnya sederhana dan bisa disederhanakan.
Seperti berbagai pihak turut bekerja sama menjaga berbagai aspek keamanan di lingkungan sekitar kita, demikian pula dengan cybersecurity. Keamanan di dunia online, dunia siber, alias Cybersecurity, bisa dan perlu kita urus bersama.
Akademisi bisa membantu menyediakan data, informasi, melakukan riset, dan edukasi publik. Pemerintah bisa membuat aturan-aturan (public policies) yang memastikan terciptanya kondisi keamanan siber yang baik. Dan yang paling penting, masyarakat, bisa membantu mendampingi dan mengawasi pemerintah, dan saling mendidik sesama dalam berbagai hal ; seperti pemakaian perangkat yang aman, selalu berpikir kritis, agar tidak mudah menjadi bulan-bulanan para penipu digital.
Dunia siber adalah dunia yang luas sekali. Tidak mungkin hanya diurus oleh pemerintah, apalagi jika dibebankan hanya ke beberapa instansi. Kita semua bisa, dan perlu ikut serta juga.
APA HUBUNGANNYA DENGAN KITA ?
Ada satu hal yang menarik ketika berbincang dengan keluarga, salah satunya dengan ibu saya, tentang insiden hacking PDNS ini. Pertanyaan beliau sangat sederhana: “apa hubungan kejadian ini dengan saya?”
Apa hubungannya antara insiden yang menimpa institusi PDNS yang sangat besar itu, dengan saya, seorang masyarakat awam, ibu rumah tangga?
Masyarakat yang cerdas tentu akan mempertanyakan hal yang sama juga ; dan wajar jika kemudian pada menarik kesimpulan yang sama : tidak ada, ah itu urusannya yang diatas, dst.
Kesimpulan tersebut sangat bisa dipahami, karena mayoritas orang masih memisahkan dunia online dengan dunia offline.
Kita mengira bahwa dunia online, dunia siber, itu adalah sebuah dunia yang jauh nun disana. Beda planet. Sedikit sekali sentuhannya dengan kita. Dan seterusnya.
Sayangnya, tidak demikian halnya.
KITA DAN CYBERSECURITY
Berkat Internet, kini dunia siber sudah menyentuh semua aspek kehidupan kita. Dunia online dan dunia offline adalah dua dunia yang saling paralel berada di ruang yang sama, yaitu dunia kita.
Rekening bank kita sudah berada di dunia siber juga. Data-data pribadi kita ada / eksis di dua dunia tersebut juga. Berbagai kegiatan bahkan sosialisasi pun kita lakukan di dua dunia secara bersamaan. Dan seterusnya.
Insiden seperti PDNS, dampaknya bisa baru muncul & dirasakan belakangan. Tapi sayangnya, kadang buntutnya ini bisa terus berlangsung bahkan sampai bertahun-tahun setelah kejadian insidennya.
Misalnya, data yang bocor dari berbagai insiden hacking / peretasan itu bisa jatuh ke tangan sindikat penipu – yang kemudian jadi bisa menelpon kita, dan lalu berpura-pura menjadi bank atau polisi atau entitas lainnya; dan bisa meyakinkan karena tahu informasi yang seharusnya rahasia.
Atau data bocor tersebut jatuh ke tangan sindikat peretas, yang kemudian memakai data kita untuk melakukan transaksi dengan berbagai pengusaha pinjol (pinjaman online). Kemudian kita yang kebingungan karena tetiba dikejar-kejar oleh para debt collector.
Dan berbagai skenario lainnya, hanya terbatasi oleh imajinasi para oknum-oknum penjahat ini.
APA YANG BISA KITA LAKUKAN ?
Sungguh mengerikan membayangkan para penjahat yang gentayangan di dunia siber tapi bisa membahayakan kita. Apa yang bisa kita lakukan?
Untungnya senjata paling ampuh untuk melawan ini sudah kita miliki ; yaitu akal sehat.
Hanya perlu sering latihan untuk menggunakannya. Seperti senjata api yang perlu latihan agar bisa digunakan dengan baik, demikian pula dengan akal kita.
Perlu sering kita latih berpikir kritis, agar tidak mudah menjadi korban penipuan. Dapat kiriman surat undangan nikah? Jangan langsung klik – cek dulu pengirimnya. Tanya ke nama yang disebutkan di undangan tersebut, apakah memang mengirim surat undangan itu, atau sebetulnya itu virus? Dan seterusnya.
Tetiba dikejar debt collector pinjol bahkan sampai ke rumah? Jangan panik dan emosional – cari tahu apa aturan terkait hal ini. Cari tahu siapa saja yang bisa membantu kita; RT, RW, Babinsa, OJK, dan seterusnya. Kontak korban-korban serupa dan saling berbagi informasi & saling bekerjasama. Dan seterusnya.
Ada tawaran menggiurkan yang rasanya mustahil? Hampir bisa dipastikan, ya, itu mustahil, dan sebetulnya adalah penipuan.
Skeptis & berpikir kritis adalah senjata utama kita semua.
APA YANG PEMERINTAH BISA LAKUKAN ?
Terkait infrastruktur IT, cybersecurity musti menjadi pondasinya. Lalu semua hal lainnya dibangun di sekitar dan berdasarkan ini.
Karena security itu adalah proses, bukan suatu alat yang bisa dibeli.
Dokumen pengadaan / tender musti ditingkatkan kualitasnya. Tidak bisa cuma menuntut sertifikasi ini dan itu; namun musti membahas sampai detail rincian terkait berbagai kegiatan cybersecurity yang perlu dilakukan. Kawan-kawan akademisi bisa membantu disini, juga yang lainnya.
Vendor mahal dan ternama bukan jaminan. Banyak yang di dalamnya bekerja dengan sangat amatiran, dan tidak paham berbagai detail teknis yang diperlukan. Pemerintah musti kritis terkait kerjasamanya dalam bidang ini.
Cybersecurity musti menjadi prioritas utama bagi semua pihak. Maka yang lainnya otomatis akan jadi bisa berjalan dengan baik.
KESIMPULAN
Insiden PDNS ini, dengan segala aspeknya yang terkait, sebenarnya pada hakikatnya adalah “wake up call”, terapi kejut.
Ini yang kena serang baru PDNS, PDN Sementara.
Bukan PDN.
PDN yang sebenarnya masih dalam proses pembangunan di beberapa kota.
Namun, PDNS saja sudah seperti ini dampaknya. Luar biasa sekali.
Musti langsung kita sadari secara kolektif : Bagaimana jika PDN yang kena serang?
Apa yang akan terjadi? Apakah negeri ini akan jadi lumpuh seketika karenanya?
Maka bersama-sama kita harus mempersiapkan ini, agar tidak terjadi lagi.
Kita harus asumsikan yang terburuk yang bisa terjadi, dan lalu mempersiapkan untuk mencegahnya.
Seperti kata pepatah, “hope for the best, but plan for the worst”
Cukup PDNS saja menjadi korbannya. Cukuplah ini menjadi pelajaran bagi kita. Jangan ada lagi.
Dipublikasikan di Koran Tempo pada tanggal 1 Juli 2024 : https://koran.tempo.co/read/opini/489011/ransomware-pdns-dan-keamanan-siber